Bitcoin Ossification Client (BOC) — Community-Defended, Minimal-Change, Adversary-Hard
Ossify the base. Keep it livable. Adapt through optional layers. That’s how Bitcoin survives adversaries who are richer than all of us, and how ordinary people keep the keys to their own money.
Bitcoin’s development process has been broken for a long time and Bitcoin’s developers have failed the community.
I have already written about this in the following article:
99% of users should have never even heard of OP_RETURN, let alone know what it does — and the fact they do means Bitcoin’s developers have failed the community.
As a developer, you would only leak implementation details onto your user base if you are:
incompetent
attacking the network
both
The fact that non-technical users have had to learn about these details is a massive failure on the part of the developers.
Now you have users taking sides on a soft-fork debate purely based on their blind faith in influencers without understanding the technicalities.
When UX abstraction fails, politics invades the base layer:
Money that requires protocol literacy isn’t money yet. If non-technical holders must parse mempool policy, witness discounts, inscription hacks, or soft-fork signaling to judge existential risk, you’ve leaked governance from experts to the masses without giving them power — just anxiety.
Abstraction debt. Bitcoin’s developers are no longer shipping “safe defaults”. That created a vacuum where influencers do protocol comms, and users pick tribes by vibes.
Legitimacy hazard. The minute regulars think “the rules can shift under me”, your store-of-value narrative becomes contingent on whoever writes/merges code, not on time. That’s a reputational tax that compounds.
In the Bitcoin ecosystem (developers, miners/pools, exchanges/custodians, state/regulators), no actor with power is optimizing for “simple, sovereign Medium-of-Exchange for the masses”. They optimize for revenue, deniability, and policy compatibility.
All of this chaos and retail anxiety caused by developers will lead more people to ETFs/custody adoption and will lessen self-custody and Medium-of-Exchange use.
If node policy changes keep enabling more and easier illegal payloads, pressure lands on runners/miners first.
Developers have to start treating Bitcoin’s users as stakeholders, not an audience they have contempt for.
If safety requires end users to follow mempool policy debates, the governance is broken.
Developers are paid to ship. Funders want visible movement; “no change” doesn’t justify grants. So maintenance drifts toward policy activism disguised as hygiene.
Why the dev process has been the preferred attack surface:
Cheaper than legislation: Defaults and “safety” framing do the enforcement work.
Plausible deniability: “We’re just improving performance”.
Captured developers is the most asymmetric attack vector - it hits sovereign users hardest, while leaving institutional wrappers unaffected.
Path dependence. Once UX, infra, and education conform to a default, reversing it is socially and economically expensive — so the ratchet holds.
So why not just run Bitcoin Knots and call it a day?
I think most would agree that running Bitcoin Knots is a much better option than running Bitcoin Core (especially v30).
The Bitcoin Core client, which is run by ~80% of nodes has become an attack on Bitcoin’s user base.
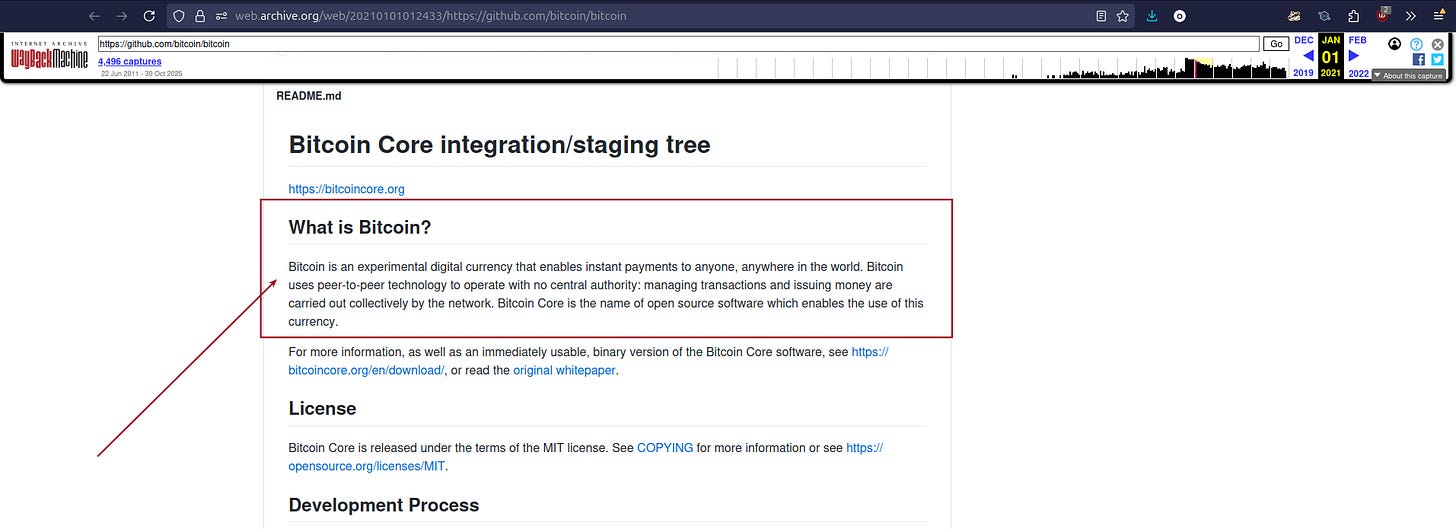
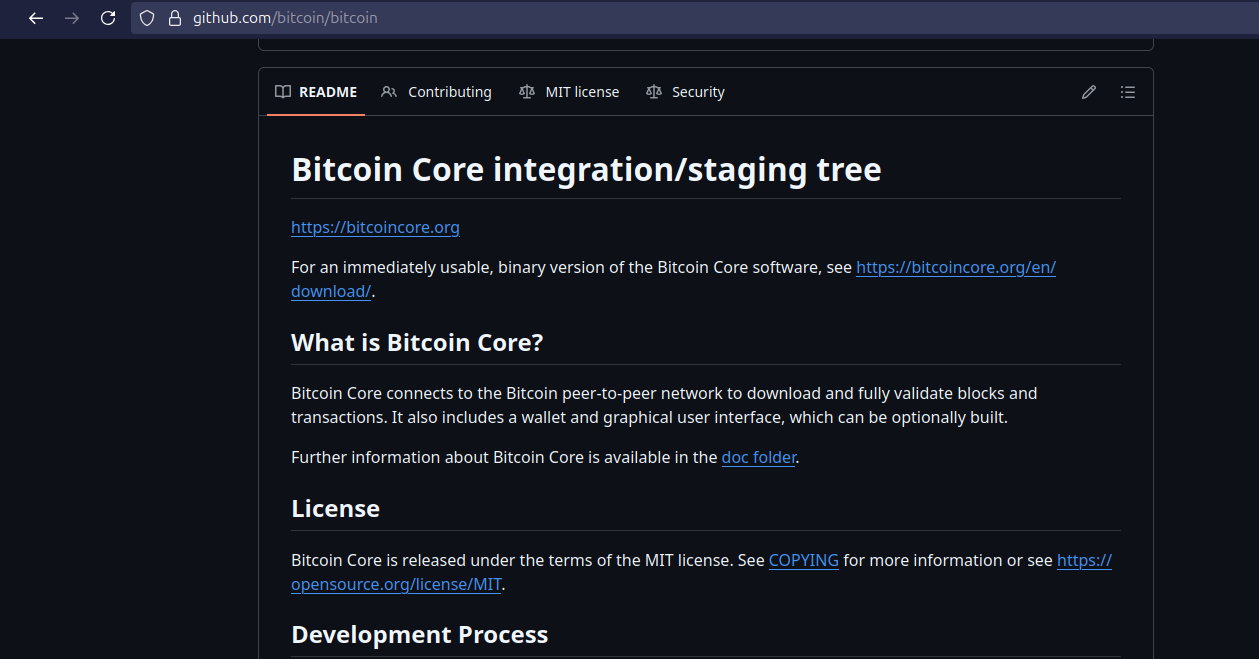
Bitcoin core’s developers have even decided to remove Bitcoin’s definition from their repository.
I wonder why that is. Could it be because the changes they’ve made to the protocol are misaligned with the definition of Bitcoin they previously used?
You can use the wayback machine (archive.org) to see what Bitcoin Core’s repository looked like before they removed Bitcoin’s definition.
And here is what the repository looks like after they’ve removed Bitcoin’s definition.
No mention of what Bitcoin is. So they are changing something they can’t define or won’t define because the definition most Bitcoiners agree with is misaligned with their updates to the protocol.
Bitcoin Core has harmed Bitcoin’s sovereign / monetary (MoE) use over time. SegWit (BIP141), Taproot (BIP340–342), Datacarrier “policy” liberalization, Replace-By-Fee evolution, Legal-risk externalities pushed onto node operators, etc.
We would need to explore these and a bunch more in a separate article. And it’s important to note that none of these changes were sold as “hurting Bitcoin as Medium-of-Exchange”.
Cheaper witness, friendlier data-paths, Replace-By-Fee normalization, relay policies favoring deep pockets, and node-operator liability drift together tilt Bitcoin toward settlement + asset rather than sovereign cash.
However, the whole Bitcoin Core v28 vs Bitcoin Core v30 vs Bitcoin Knots debate is a massive False Trichotomy.
A False Trichotomy is a logical fallacy that presents three options as the only possible choices when, in fact, there may be other alternatives available.
This oversimplifies the situation and misleads the audience into thinking they must choose among the limited options presented.
You give people a worse option (Bitcoin Core v30) and a bad option (Bitcoin Core v28, Bitcoin Knots) to choose from and there is no right answer.
Blind trust in Bitcoin Core developers is very dangerous, in the same way blind trust in Bitcoin Knots developers is.
Humans can be fallible, corrupt or both.
Recent changes to the protocol have done more harm than good.
There is a need for a client that is more battle-tested, more secure, leans toward ossification and builds more consensus if changes need to be implemented (e.g. existential bugs).
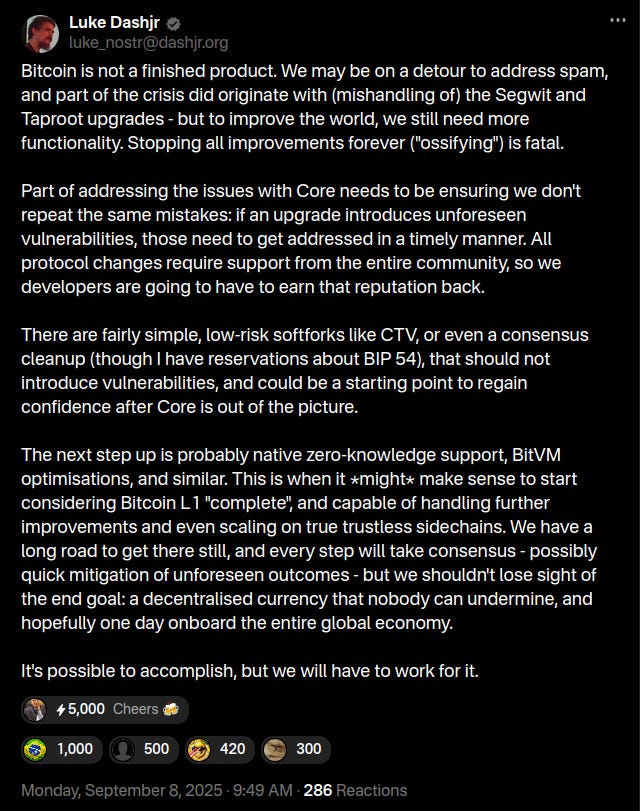
If you tell me:
“Bitcoin is not a finished product. We may be on a detour to address spam, and part of the crisis did originate with (mishandling of) the Segwit and Taproot upgrades — but to improve the world, we still need more functionality. Stopping all improvements forever (”ossifying”) is fatal”.
Then you’re going to have to provide more context.
Is ossifying fatal because:
of failed changes developers have made to the protocol,
or is ossifying fatal because it doesn’t allow for a use case you want to implement,
or is ossifying not fatal at present?
And of course, I agree that ossifying into brittleness is a real problem and something to be considered. The more we wait, the more developers mess with the protocol and continue to undermine Bitcoin’s sovereign / monetary (MoE) use.
This is where I took the quote from:
Bitcoin development and “Bitcoin improvements” have turned into a complete shit show.
You have people with full time jobs, with a good chunk of their savings (time and energy) invested into Bitcoin getting bombarded with technicalities by developers.
Most of these developers don’t understand psychology, finance, geopolitics, history, and human incentives, and have zero capability to understand and game theory adversarial thinking.
If we are currently in a complete shit show protocol-wise and you start talking about other “improvements” you want to make to the protocol, it shows that you have very close to zero ability to read the room.
The most dangerous attack vector to Bitcoin is developers making changes to the protocol that harm decentralization and impede its Medium-of-Exchange use.
This article proposes a Bitcoin Ossification Client (BOC) alternative.
Bitcoin Ossification Client (BOC) — Community-Defended, Minimal-Change, Adversary-Hard
0) Premise — Define Bitcoin operationally (so we can defend it)
Bitcoin is not a brand or a GitHub repository. Bitcoin is a set of operational guarantees that users choose to run:
Monetary finality: 21M fixed supply and halving cadence; no dilution via semantics, fee rebates, or “creative” data paths.
Commodity verifiability: Any unpermissioned peer can fully verify on consumer hardware within strict time/storage/bandwidth/CPU envelopes.
Censorship resistance via cost: State-level adversaries face rising economic cost to block/reorder valid settlement.
Self-custody at retail scale: It remains practical and safe for ordinary users to self-custody and run a full-verifying node.
BOC’s purpose is to freeze those guarantees at the base layer and only change code to repair existential breakage. Everything else moves up the stack (L2/L3, wallets, services).
If a proposed change cannot convincingly preserve these guarantees under realistic adversaries, it does not ship — and it does not get funded.
1) Non-Negotiables vs Governables (What BOC considers “red” and “amber”)
1.1 Invariants (red; never change unless not changing is existentially worse)
21M schedule and halving cadence.
Proof-of-Work (SHA-256 family) as the consensus class.
UTXO model and spendability semantics.
Decentralization envelope: publish hard ceilings per release for initial sync time, steady-state CPU/RAM, chainstate/disk size, bandwidth. Users must verify on commodity hardware with margin.
Miner neutrality: the protocol does not deputize miners as content police.
Touch these and you must prove that not changing them is worse and ship a clean rollback path. Expect “no”.
1.2 Governable parameters (amber; may adjust inside tight bounds)
P2P relay and mempool policy defaults; block/weight policy within the node-cost envelope; Denial-of-Service guards; unambiguous fee/relay heuristics.
Network hygiene and privacy improvements that lower centralization risk and adversary leverage.
Any amber tweak must ship quantified trade-offs, pass adversary simulations, and remain explicit/opt-in where possible. No silent defaults that widen attack surface.
2) Adversary Model (design for enemies who actually exist)
BOC assumes and tests against:
Infinite-Fee Spammer: state-backed actor paying any fee to bloat UTXO/chainstate/bandwidth and raise node costs.
Legal-Contamination Attacker: embeds contraband/malware to create regulatory risk for node runners/miners/hosts.
Template/Policy Cartel: relay/mining power steered by a few vendors/providers or policy clients.
Cloud & App-Store Choke: de-peering, ToS bans, distribution throttles that kneecap sovereign nodes/wallets.
Paperization Bloc: ETFs/exchanges/treasuries that externalize operational costs and push users off L1.
If a change increases leverage for any of these, it is net harmful.
3) Must-Pass Acceptance Tests (no pass, no merge, no funding)
Node-Cost Envelope: reproducible before/after profiles for CPU, RAM, disk, bandwidth under normal and adversarial loads. Median user stays in budget with margin.
Sovereign Survivability: simulate spam/legal payloads/miner-policy drift. Costs for sovereign runners must not rise; legal blast radius must not widen.
Fee-Market Integrity: no subsidized non-monetary paths that crowd out settlement; no hidden resource asymmetries.
Rollbackability: documented revert path (flags/versionbits/policy switches).
Economic Neutrality: change must not confer structural advantage to custodial wrappers (ETFs, Treasuries, etc.) over self-custody.
Clarity of Scope: consensus vs policy separation; list impacts on old nodes; list failure modes if a minority rejects.
More on consensus vs policy separation: You can think of consensus rules as the laws of Bitcoin’s physics — every node must follow them exactly the same way or it falls out of sync with the universe. So consensus rules are immutable facts that define what a valid block or transaction is. Policy rules are more like local driving habits — each node or miner can choose stricter rules for what they relay or mine, but those don’t change what the network as a whole considers valid. They shape behavior and performance, not validity.
No public simulations. No quantified envelopes. No merge.
4) Why a BOC-style client is best for users (and requires least trust)
Minimum trust surface: ships less policy, not more; hard line between consensus and relay/mempool; defaults bias to safety and denial for non-monetary data.
Commodity hardware guarantee: every release is signed with hardware cost attestations; you can verify with cheap gear.
Transparent veto: users see exactly how to refuse unsafe changes without being orphaned.
Audit-ready process: dual independent implementations for any semantics; open adversary simulations; public red-team windows.
Clear social contract: one semantic change per activation; no bundling; no “surprise defaults”.
Optionality preserved: anything not essential to base-layer settlement moves to L2/L3 and wallets — where choice/competition belong.
5) How to not ossify into brittleness
Ossification ≠ paralysis. It means tight base-layer scope plus fast patch lanes for existential issues.
Dedicated “Hotfix Lane”: pre-approved activation/rollback mechanism for breaks or consensus bugs, with rehearsed drills.
Pluggable policy modules: relay/mempool logic out of core in signed, optional modules; explicit local overrides with loud UI warnings.
Canary & shadow deployments: optional dark-mode flags to simulate policy changes on test nets and shadow nodes without touching consensus.
Independent conformance tests: spec + vectors maintained by two unrelated teams; client must pass vectors each release.
L2/L3 acceleration: publish “push-up-the-stack” guidelines; fund wallet/L2 experiments aggressively so innovation happens off L1.
6) Problems BOC addresses in Bitcoin Core / Knots (what’s broken in practice)
This is not personal; it’s about incentives and attack surface.
Policy creep & ambiguity: shifting mempool/relay defaults blur the line between policy and consensus; users cannot tell what’s safe.
Silent expansion of attack surface: permissive defaults for large data carriers and witness tricks invite legal contamination and cheap DoS vectors — raising costs for sovereigns.
Inadequate adversary simulations: optimistic “free-market” framing underweights state-scale attackers who can pay any fee to force externalities onto nodes.
Centralized social gravity: single-repo culture concentrates agenda-setting; bundling/hurry-up merges create de facto governance outside explicit user consent.
Cloud/app-store fragility ignored: binary distribution and discovery flows depend on a few platforms whose ToS can shift overnight.
Mixed messaging: UX forces users to learn mempool trivia; politics bleeds into L1; paperization accelerates as retail flees complexity.
Knots partial mitigation, not cure: Knots is closer to user interests on policy, but it still inherits Core’s social gravity and lacks a formally published node-cost envelope and acceptance-test discipline.
BOC fixes these by shrinking defaults, publishing cost budgets, formalizing veto paths, and refusing policy that externalizes costs onto sovereigns.
7) Governance: who decides, when, and how
7.1 When BOC will even consider touching semantics
Safety: consensus bug / halt vector.
Liveness: persistent congestion that annihilates small sovereign users after exhausting policy-level mitigations.
Security economics: clear medium-term erosion of fee-market security with no policy fix.
7.2 Veto is multiparty (observable, not vibes)
Economic majority: merchants/exchanges/payment processors — measured via relay/template usage, client fingerprints, settlement endpoints.
Sovereign quorum: geographically diverse, non-cloud-clustered nodes can adopt without hardware upgrades.
Miners alone are not sufficient. Dev repos alone are not sufficient. Require multi-constituency ACK.
7.3 Process minimums (or it’s illegitimate)
Public threat model, open harness, attack simulations.
90-day public comment + 30-day red-team window.
Dual independent implementations before activation.
One semantic change per BIP (Bitcoin Improvement Proposal). No bundling.
8) Abstraction Debt we are paying down (UX and comms)
Safe defaults, not surprise defaults: if a path raises legal/DoS risk (e.g., large data carriers), default to deny; any override is explicit and local.
Hard line in code and docs: consensus vs policy is unmistakable; users do not need mempool lore to be safe.
Public risk dashboard: live UTXO growth, chainstate bloat, relay bandwidth, cloud/node centralization. Users see cost and trade-offs in plain English.
9) Immediate Policy Stance (no consensus changes required)
Moratorium on new data-carrying mechanisms at L1 until adversary sims show lower total risk to sovereigns.
Tighten default policy to minimize legal/DoS vectors; keep overrides explicit and local — never silent.
Protect sovereign operators: per-release target hardware budgets; refuse changes that breach them.
Document veto paths for economic nodes and sovereign quorums; minority refusal remains safe.
Communicate via invariants: what cannot change and when reconsideration is legitimate (only existential).
10) Red lines and green lines (in plain language)
Reject by default
Any change that raises minimum node cost beyond consumer hardware.
Subsidized non-monetary data at scale, even “fee-paid”.
Safety that depends on miner altruism or centralized policy clients.
Bundling multiple semantics under one activation switch.
Ambiguous authorship of risk (who pays if it backfires?).
Advance by default
Policy tweaks that shrink legal/DoS surface and reduce node costs with zero consensus impact.
P2P upgrades that improve privacy, resilience, and reduce cloud choke points.
Tooling for self-custody, inheritance, Proof-of-Reserves, and merchant UX — off L1, big impact, low risk.
11) Multi-Implementation Funding & Accountability (de-center any one repo)
We don’t tell anyone what to write. We fund what we will run.
Funding criteria: grants flow to implementations that (a) publish acceptance-test results, (b) obey invariants, (c) meet node-cost budgets, (d) separate consensus/policy cleanly.
Diversity rule: no single client >40% of observed economic endpoints (relay/template fingerprints). If exceeded, redirect funding to competitors until balance returns.
Bug-bounty market: standing bounties for (a) consensus safety issues, (b) policy vectors raising legal/DoS risk, (c) deviations from invariants. Reports public by default.
Conflict disclosures required for funded maintainers.
Release attestation: each release ships with hardware-cost attestations + adversary-sim results signed by two independent teams.
12) BOC Architecture and Release Discipline (what you get if you run it)
Strict consensus kernel: small, auditable, test-vector driven; no policy in the kernel.
Policy as signed modules: relay/mempool packaged separately, version-pinned, off by default beyond safe baseline.
Deterministic builds + multi-party signing: reproducible binaries; two independent build farms must match before publish.
Sovereign readiness certification: each release carries a simple badge: “Runs on X CPU/RAM/disk; sync ≤ Y hours”.
Explicit flags, loud UX: anything that widens attack surface requires explicit local enablement with descriptive warnings.
Shadow nets: permanent adversary nets to replay spam/legal contamination/policy cartel scenarios against candidates.
13) Community Execution Plan (what users and funders can do now)
Publish the invariants as a signed message; get endorsements from wallets, merchants, pools, infra.
Stand up a neutral test harness anyone can run to reproduce acceptance tests.
Create a transparent grants scoreboard and route BTC to implementations that hit the bar.
Pay reviewers and dissenters, not just mergers — reward people who find regressions.
Default innovation to L2/L3. If it’s not core to settlement/verifiability, push it up the stack.
14) If we do not tighten governance (what happens)
Paperization accelerates: sovereign fear → ETFs/custody. SoV survives; MoE atrophies.
Policy capture migrates to perimeters: app stores, clouds, and banks set rules under ToS rather than code.
Legal choke-points widen: a contamination scandal outsources governance to courts/cloud Acceptable Use Policies — the worst venue for sovereignty.
Retail loses the plot: arcane mempool trivia replaces trust; users quit running nodes.
15) Principle of Operation (for everyone to internalize)
Don’t trust — verify the invariants.
Incentives > ideals: block rich attackers from buying externalities that poor users must carry.
Control > fairness: split veto power; never let miners or a dev council gain de facto control via policy leverage.
Stability > truth: choose quantified envelopes and clamps over ideology wars.
Revealed preference: users run what they trust. Fund the clients that keep trust cheap.
16) Developer & Maintainer Compact (voluntary, but tied to funding)
If you want community funding and default adoption, you agree to:
Ship quantified node-cost and adversary simulations per release.
Separate consensus from policy in code and comms.
Avoid bundling semantics; one change/one flag discipline.
Support dual-implementation and independent test vectors.
Respect published invariants and the decentralization envelope.
No one is forced; we simply choose to run and fund those who uphold these terms.
17) “What Bitcoin Is” (front-page text BOC shows to every user)
Bitcoin is a fixed-supply, Proof-of-Work-secured, UTXO-validated settlement network that anyone can fully verify on consumer hardware. Its base layer resists censorship by making it costly — not by trusting gatekeepers. Its rules are simple, explicit, and operationally testable. If a change makes sovereignty harder, or hands control to perimeters, it isn’t Bitcoin.
Why Bitcoin Ossification Client (BOC) wins for users
It minimizes the trust you place in maintainers and defaults.
It keeps verification affordable and boring.
It draws a bright line between settlement rules and relay policy.
It gives you a clear, peaceful veto without social warfare.
It channels innovation off L1 so L1 can keep carrying people’s life savings.
Ossify the base. Keep it livable. Adapt through optional layers. That’s how Bitcoin survives adversaries who are richer than all of us, and how ordinary people keep the keys to their own money.
More context: