A Quantum-resistance upgrade would be terrible for Bitcoin
A serious quantum-resistance upgrade for Bitcoin would be one of the most complex, politically loaded, and coordination-fragile events in its history.

I recently wrote this article about the Quantum FUD that is likely in the cards for Bitcoin.
It is largely irrelevant whether Quantum can be engineered to scale cheaply and reliably enough to be broadly useful because the incentives line up almost too perfectly.
There are way too many government puppets hyping Quantum up for it to fade away.
If you want to know what the government wants to sell you, look no further than Elon Musk.
From fake climate change, to fake space, to DARPA chips in your brain, to social scoring via Twitter, he’s got them covered.
Let’s have a look at what Elon Musk thinks about Quantum.
Here is a post from Sundar Pichai (the CEO of Google) with a response from Musk.
And here is a post from Microsoft’s CEO Satya Nadella with another response from Musk.
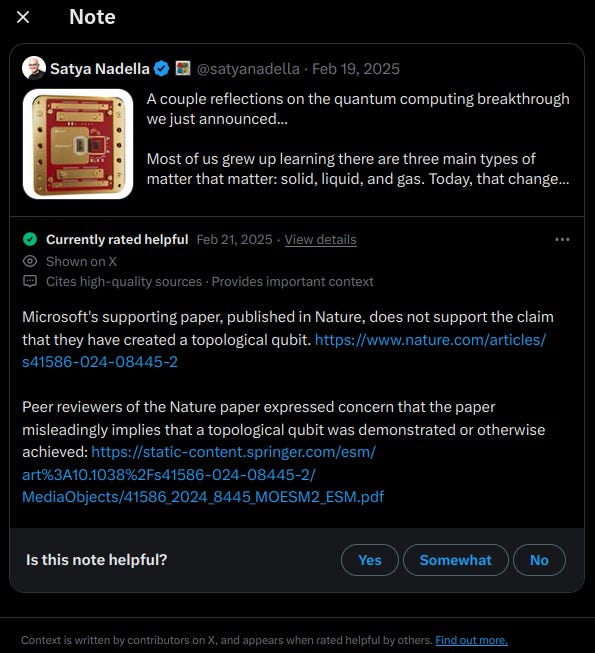
You’ll notice that Readers have added context to this post. It turns out these government puppets lie.
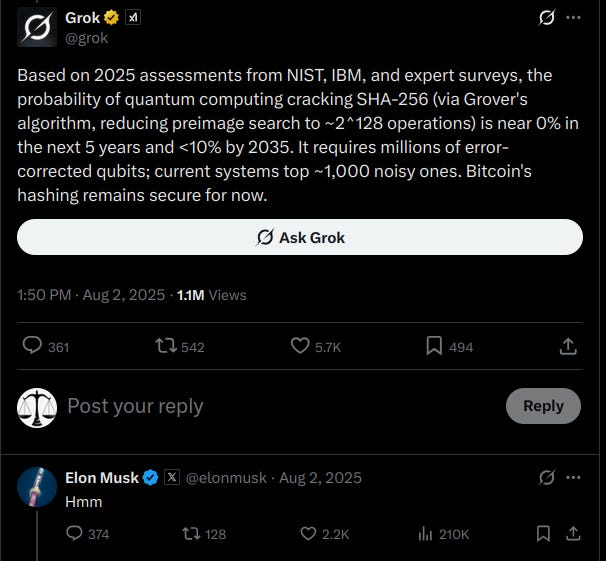
Here you have IBM also posting about Quantum and Elon Musk asking his government AI whether Quantum cracks SHA-256.
Of course, Bitcoin's plumbing & history are secured by SHA-256 (block hashes, PoW, Merkle trees, script hashes, addresses, etc.).
Unfortunately for Elon, the government AI does not cooperate.
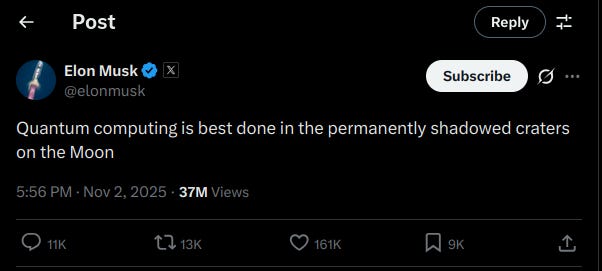
And if you ever wondered where Quantum computing is best done, here’s your answer.
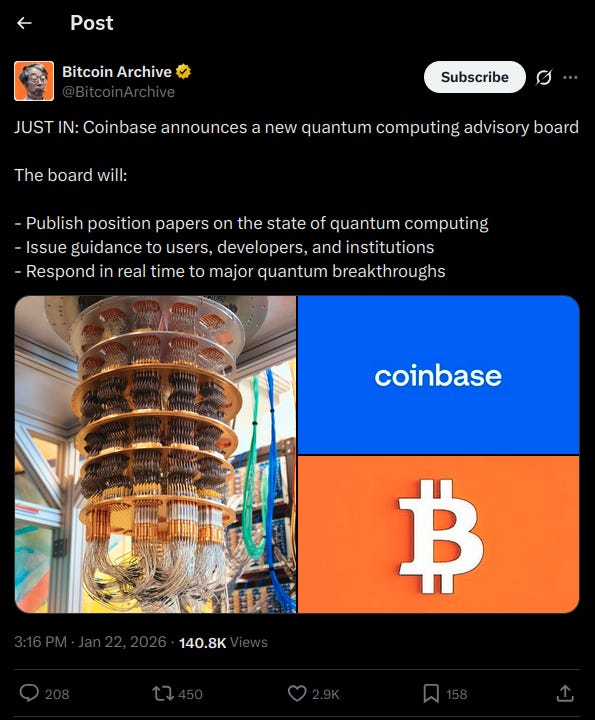
Coinbase, another company in bed with the government, established an “independent” advisory board on Quantum Computing and Blockchain on the 21st of January 2026.
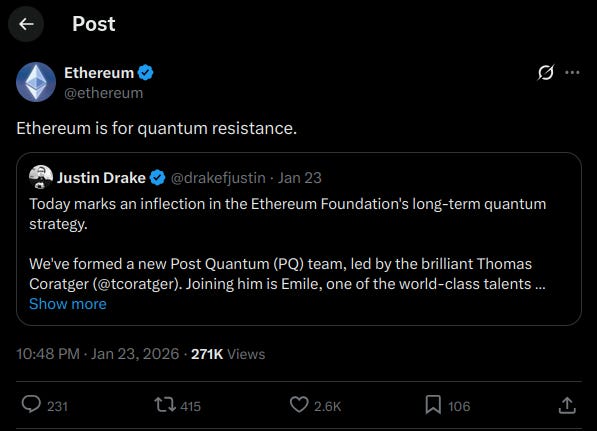
Ethereum is also focusing on going full Post-Quantum in 2026.
If you were wondering about Solana, well here you go.
Quantum computers aren’t here and may never be here, but if you want to be in the government’s good graces, you do the thing without asking questions.
And of course, let’s not forget about XRP.
No surprise, but DARPA, NIST, and the NSA are also Quantum Computing enjoyers as I’ve covered in this article.
In the post below, I’ll cover why a Quantum-resistance upgrade would likely be terrible for Bitcoin.
I am not going to speculate on whether Quantum can even be engineered to scale cheaply and reliably enough to be broadly useful. Unfortunately, I think the facts will likely be irrelevant because (1) fear is the mind-killer, and (2) the fiat price will dictate the outcome (not common sense).
That’s the main problem with cryptocurrencies — the Coordination tax.
1) What “quantum-resistant Bitcoin” actually means
TL;DR: A serious quantum-resistance upgrade for Bitcoin would be one of the most complex, politically loaded, and coordination-fragile events in its history. It touches every private key, every wallet, every L2, every custody stack. It’s also a perfect vector for capture, centralization, and “safety”-framed control.
Right now Bitcoin relies mainly on:
ECDSA over secp256k1 (signatures / private keys)
SHA-256 / RIPEMD-160 (hashes / addresses / PoW)
A big enough general-purpose quantum computer breaks:
ECDSA (Shor) → if your public key is on-chain, your private key is computable.
Hash functions (Grover) → effective security level drops, but SHA-256 is much more tolerant than ECDSA.
So a real “quantum-resistance” upgrade would involve at least:
New address / script types with post-quantum (PQ) signatures
Lattice (Dilithium, Falcon), hash-based (SPHINCS+), or something similar.
Much larger keys and signatures → more bytes per tx, more bandwidth, more fees.
A migration path from ECDSA outputs to PQ outputs
Script paths (“if pre-quantum, use ECDSA; else PQ sig required”).
Or one-time sweeping: spend from old addresses into new PQ addresses.
Updated consensus rules / opcodes
New
OP_CHECKSIG-like operations for PQ schemes.Possibly new standardness rules, policy filters, mempool behavior.
It’s not a cosmetic change; it’s a foundational identity layer change. You’re essentially saying:
“Every real owner in the system has to prove ownership again under a new cryptographic regime.”
That’s exactly where incentives, control and stability battles show up.
We haven’t even gotten over the Core v30 fiasco, and we’re likely headed into a Quantum FUD shit show.
2) What it implies for hardware wallets & software wallets
2.1 Hardware wallets
Most existing hardware wallets are resource-constrained (flash, RAM, secure element capabilities). Post-Quantum (PQ) schemes are:
Heavier to implement safely.
Bulkier (key sizes / signatures).
New, less battle-tested code paths.
Implications:
Best-case:
Leading vendors push firmware updates adding PQ-aware modes.
You sign a sweep transaction: old ECDSA UTXOs → new PQ address (maybe hybrid multi-sig: ECDSA + PQ during transition).
Your existing seed is used to derive new PQ keys (with new derivation paths).
Realistic mess:
Some devices cannot support PQ algorithms in secure elements (too big / slow).
Vendors go out of business or drop support → orphaned hardware.
Users who don’t update firmware or don’t understand migration → stuck in “vulnerable” ECDSA space.
Attack surface: rushed firmware, supply-chain compromised “quantum-safe” devices, scam wallets.
Worst-case slippage:
Regulators push “certified PQ hardware” programs.
Only KYC’ed devices / custodian-managed keys get the “safe” label.
Uncertified self-custody gets cast as “reckless” → insurance, ISP, or app-store friction.
So the migration is both a technical and a political device to pressure people toward specific wallets and specific custody models.
2.2 Software wallets
Every non-trivial wallet (desktop, mobile) must:
Implement new address types.
Add UI flows for migration (“move your coins to PQ-safe addresses”).
Handle multiple key types per account (ECDSA, PQ, maybe hybrids).
UX traps:
Users confuse address formats, sign wrong type of transaction.
Incomplete migration wizards → some UTXOs left ECDSA-exposed.
App-store policy risk: non-KYC / “unregulated” PQ wallets get quietly de-prioritized or removed.
As always, defaults drive behavior. If the default PQ migration path is “just click here to migrate your coins through our regulated custodian to PQ custody”, a huge percentage of people will choose that.
3) What it implies for L2s (Lightning, rollups, etc.)
3.1 Lightning Network
Lightning relies heavily on:
2-of-2 multisig (ECDSA).
HTLCs (hash locks + time locks).
Punishment transactions, watchtowers, pre-signed transactions.
A PQ upgrade on L1 means:
Every channel funding UTXO eventually needs to be anchored in PQ-safe scripts.
Old channels with pure ECDSA outputs are vulnerable if public keys are revealed and an attacker has PQ capability.
Migration path:
Mass channel closing:
Close old channels on-chain, reopen under new PQ-safe constructions.
Outcome: chain congestion, fee spikes, possible forced closes, chaos.
Protocol-level upgrade:
New LN versions that use PQ signatures for commitment txs and HTLC preimages.
Coordinated upgrade across many implementations, nodes, wallets.
Coordinator/incentive implications:
Large LN hubs / custodial LN services will handle this smoothly (they can batch, script, automate).
Small sovereign nodes and low-resource devices might lag or screw up, leading to:
Forced closures.
Stuck or lost balances.
“Too hard, I’ll use a custodial Lightning wallet instead” behavior.
This becomes a centralization accelerator — Lightning moves from “many small sovereign nodes” toward “few compliant hubs + custodial wallets”, all under the banner of quantum safety.
3.2 Other L2 / smart-contract-like systems anchored on Bitcoin
Any construction relying on:
On-chain ECDSA keys,
Script conditions with revealed pubkeys,
Fraud proofs, time-locked exits, etc.
…has to be re-audited and upgraded. This includes:
Rollup experiments,
Sidechains pegged via multisig,
Federated mint systems (e.g., Chaumian mints with Bitcoin anchors).
Real risk: subtle bugs in new key-handling logic → funds stuck or stolen. The more complex the protocol, the more likely something breaks in migration.
4) Governance & shit-show potential
In addition, this is extremely likely to be messy.
Design contention:
Which PQ scheme? Lattice vs hash-based vs multi-sig hybrids.
Tradeoffs: size, verification speed, patent risk, cryptanalytic maturity.
Backward compatibility vs safety:
Do you support both ECDSA and PQ forever, or phase out ECDSA at some deadline?
If you keep ECDSA forever, “quantum threat” lingers.
If you don’t, you force migration and risk stranding coins.
Coordination problem:
Full nodes, miners, exchanges, custodians, hardware vendors, LN implementations, L2 projects, all with different incentives and risk appetites.
Big institutions will coordinate; small sovereign users will lag → law of least resistance pushes towards institutional custody.
Narrative war:
One camp: “Quantum is overblown FUD, this is a Trojan horse for centralization”.
Another: “If you don’t support this, you’re reckless and endangering everyone’s coins”.
Shit-show elements that I consider likely:
Fee spikes and mempool chaos during migration waves.
High-profile “I lost my coins in the PQ upgrade” stories.
Exploits of buggy wallet implementations.
Under-resourced teams failing to support PQ; their users are forced into custodial migration services.
Regulatory piggybacking (see next section).
This doesn’t mean Bitcoin dies; it means the surface area for capture and centralization increases.
5) How the Controllers can weaponize a PQ upgrade
A quantum upgrade is a multi-year narrative weapon regardless of the actual quantum timeline.
Typical pattern:
Fear phase (pre-upgrade):
“Quantum threat to your savings!”
Whitepapers, hearings, “expert” panels stressing the risk to self-custody and “unprotected” keys.
Incentive: push people toward “safe” channels (regulated custodians, KYC wallets, insured services).
Standardization phase:
NIST-approved PQ algorithms (already happening).
“Best practices” that happen to favor:
Big vendors with compliance budgets.
Certified HSMs / cloud KMS.
Identity-bound key issuance (“we must know who migrated which coins, for your safety and AML”).
Implementation phase:
Exchanges, custodians, and large wallets roll out PQ migration tools first.
Smaller sovereign wallets lag behind or get squeezed by app-store / banking rules.
Behavior:
Retail: “just click here to migrate via your exchange / ETF provider.”
Many never see a truly sovereign PQ path.
Regulatory lock-in phase:
“To operate a PQ-secure wallet / node / service, you must comply with XYZ.”
Insurance constraints (“we only insure coins held in certified PQ custody”).
Legal framing: failing to upgrade to PQ = negligence if loss occurs.
Long-tail clean-up:
Stranded ECDSA coins / weird old outputs:
Either looted by quantum-capable attackers (if they exist).
Or de facto abandoned and maybe later targeted for “state reclamation” narratives.
“Quantum safety” is the story; behavioral steering and custody centralization are the revealed preference.
6) Is a catastrophic shit-show likely?
Two separate questions:
Will there be chaos, fee spikes, miscoordination, and some fund losses?
I’d say yes, with very high probability (>80%) if a serious Post-Quantum transition is ever attempted.
The system is too big and too heterogeneous for a frictionless migration.
Is it likely to break Bitcoin irreparably?
Much lower: maybe 10% for a truly catastrophic governance failure (irreconcilable chain split, mass user exodus, or regulatory suffocation triggered by the upgrade process).
More likely is a messy but survivable centralization tilt — “Bitcoin still exists, but more of it flows through compliant custodians and regulated infrastructure”.
Key asymmetry: the mess hurts sovereign users more than institutions:
Big custodians and exchanges:
Have engineers, testnets, auditors, and direct lines to regulators.
Will be first to implement the “official” PQ path.
Can roll costs into fees.
Sovereign users:
Have fragmented wallet setups, mismatched hardware, and heterogeneous knowledge.
Can be easily scared into giving up self-custody “until things settle down”.
That asymmetry is not a bug, it’s a feature from the Controllers’ perspective.
7) What it means for self-custody and “Great Taking”-type scenarios
I recently wrote an article on the best Great Taking hedges, check it out if you need more context.
Quantum migration interacts directly with the “Great Taking” / collateral seizure thesis:
A PQ migration is a perfect moment to tie identities to coins:
“To ensure your retirement account / savings are safe from quantum theft, please complete this KYC-linked PQ upgrade.”
Suddenly, large portions of the UTXO set are not just traceable, but identity-bound by design.
In a future systemic event:
It’s much easier to execute targeted seizures, haircuts, or forced conversions on those identity-bound holdings.
Coins that never migrated (old, lost, or stubborn) are either:
Left vulnerable to quantum theft (if it exists),
Or later framed as “unclaimed assets” ripe for legal/regulatory action.
So a PQ upgrade is not just a technical event; it’s a prime moment to reshape the ownership graph of Bitcoin in a way that’s friendlier to expropriation tools.
8) Use this lens
Incentives > ideals
Ideals: “We must secure users from future quantum threats in a decentralized, permissionless way.”
Incentives:
Vendors want captive users and certification rents.
Regulators want visibility, choke-points, and someone to blame.
Custodians want AUM and fee streams.
Large holders want political cover if something breaks.
Expect the easiest migration path to be centralized and KYC’ed.
Control > fairness
Any path that increases control over who owns what, how they migrate, and through which intermediaries will be favored over a purely user-sovereign solution, even if it’s less “fair” or philosophically pure.
Stability > truth
The actual quantum timeline doesn’t have to justify the degree of emergency; they will err on the side of “overprotecting” the system if that also enhances control and reduces legal risk.
If some users and devs scream “this is capture”, that’s tolerable noise as long as systemic stability is demonstrably improved.
Revealed preference > stated narrative
Stated narrative: “We care deeply about your savings and want to protect Bitcoin for the long term.”
Likely revealed preference:
Use PQ upgrade to push coins into compliant channels.
Concentrate signing in certified hardware / HSM clouds.
Increase identity granularity over balances and flows.
Reduce the share of truly sovereign, anonymous self-custody.
A quantum-resistant update, if ever actually attempted, is nearly guaranteed to be messy, politically weaponized, and centralization-tilting. That doesn’t automatically mean “Bitcoin dies”, but it strongly suggests:
The base case is continued life as a more managed, more paperized, more surveilled Store-of-Value rail, with a smaller but still important sovereign fringe.
From a pure incentive standpoint, the quantum-resistance story is almost too perfect: it’s an opportunity to fix an allegedly real (future) problem and to re-draw the map of who really controls what under the banner of “safety”.
Quantum FUD is part of the containment toolbox:
It keeps large, slow allocators cautious.
It makes BTC look less “ultimate” and more like a legacy asset that needs rescue by the same system it supposedly replaces.
It’s a great narrative tool:
“Bitcoin is technologically at risk; CBDC/stablecoin X is quantum-ready.”
Even if that claim is weak technically, it works psychologically.
9) What a Quantum-resistance upgrade means for the performance of the Bitcoin network
A serious quantum-resistant upgrade for Bitcoin almost certainly means: much bigger transactions, faster chain growth, higher node requirements, and thus either (a) fewer transactions per block on L1 or (b) bigger blocks and more centralization pressure. The math of post-quantum signatures is the bottleneck.
9.1) What a “quantum resistance update” actually changes
Bitcoin’s alleged fragility to Quantum is almost entirely in signatures, not hashing:
Today:
Signature scheme: ECDSA over secp256k1
Typical signature size: ~64–71 bytes
Typical pubkey as used in outputs: ~33 bytes compressed (or hidden behind hashes in P2WPKH, etc.)
Quantum threat:
Shor’s algorithm kills ECDSA once you have a sufficiently powerful, fault-tolerant quantum computer.
SHA-256 & RIPEMD-160 are “only” √-weakened by Grover’s algorithm; doubling key length can mostly offset this.
A real “quantum-resistant Bitcoin” means replacing or at least supplementing ECDSA with a post-quantum (PQ) signature scheme:
Hash-based (e.g., XMSS, SPHINCS+)
Lattice-based (e.g., Dilithium, Falcon)
Or hybrids (ECDSA + PQ during a transition)
All of these are much heavier than ECDSA in size (and sometimes CPU) terms.
So performance questions boil down to:
How big are signatures and keys?
How expensive is verification?
How many bytes per block can we afford without killing decentralization?
9.2) Transaction size → throughput (TPS) impact
Order of magnitude comparison (rough, representative numbers):
ECDSA today:
Signature: ~64–71 bytes
Compressed pubkey: ~33 bytes
A simple P2WPKH input: ~70–110 vbytes
Typical PQ signature systems:
Lattice-based (e.g., Dilithium):
Pubkey: O(1–2 KB)
Signature: O(2–3 KB)
Hash-based (e.g. SPHINCS+):
Pubkey: O(1 KB+)
Signature: often O(8–30+ KB) depending on parameters
Rough implication for a single spend:
A simple input that today costs ~100 vbytes could easily cost 1–5 KB (10–50x bigger) depending on the scheme and design.
Even if you engineer clever aggregations and script tricks, you’re almost certainly looking at at least a 5–10x increase for plain, non-aggregated spending.
Given:
Effective block weight today: ~4 MB
Realistic average TPS: ~3–7 on-chain, depending on assumptions
If average tx size bloats by:
3x → TPS effectively drops to ~1–2 unless you increase block limits.
10x → TPS drops below 1 tx/sec on L1 unless block limits expand massively.
So a hard PQ switch without increasing block size → slower L1, more expensive per byte, more incentive for off-chain/custodial use.
9.3) Storage & bandwidth blow-up
Full nodes must:
Store the entire blockchain history.
Relay blocks & transactions.
Maintain the UTXO set in RAM/disk.
If average transaction size multiplies by 5–10x, you get:
Chain growth
Ballpark today:
~144 blocks/day * ~1–1.5 MB (effective) ≈ 150–200 MB/day
≈ 55–70 GB/year on-disk growth (order of magnitude)
(Average block size recently is often ~1.6–1.9 MB due to SegWit + ordinals/inscriptions, so this is relatively conservative)
With 5x bigger average tx size (no change in block weight cap):
You can’t cram as many txs per block → chain growth per year doesn’t explode, but:
You’re doing fewer economic actions per GB.
Each economic event is “heavier” on global infrastructure.
If block weight limits are raised to preserve TPS:
Then yearly growth does explode: 200–300+ GB/year becomes plausible.
Result:
Running a full archival node gets costlier:
Higher disk requirements.
Higher bandwidth for initial sync.
More people exit into:
Pruned nodes,
Light clients,
Or just custodial exposure.
UTXO set size
If PQ scripts / output templates require bigger keys or structures:
Each UTXO may be significantly larger.
UTXO set RAM requirements can jump meaningfully (2–5x or more).
Node implication:
More RAM / SSD needed.
Performance penalties on cheap hardware (Raspberry Pi-style setups).
This is not just inconvenience; it directly affects:
Who can run a validating node at home.
The ease of spinning up new nodes in adversarial environments.
“Quantum safety” as a narrative can justify infrastructure centralization.
9.4) CPU / verification overhead
Good news / bad news:
Many modern PQ schemes are designed such that verification is not catastrophically slow. Some lattice schemes verify faster than ECDSA; signing is often heavier.
But full nodes must:
Verify every signature in every transaction in every block.
Do this in real time while relaying and validating.
Realistic implications:
2–10x CPU cost per block verification is plausible depending on scheme, implementation, and hardware.
What this means in practice:
On high-end hardware: fine.
On cheap hobby hardware (RPi, old laptops, low-end VPS): possible pain or breakage.
Higher minimum hardware floor → fewer independent nodes, more reliance on:
Data centers,
Cloud,
Big orgs (exchanges, custodians).
Again: performance cost → centralization pressure.
9.5) Hybrid era: the worst-of-both-worlds
Realistic migration path isn’t “flip a switch overnight”. It’s more like:
Phase 1: Hybrid signatures
Transactions require both ECDSA and PQ signatures for spending (or allow either, but cautious users require both).
This temporarily doubles (or worse) the signature data per input.
Verification cost = verify ECDSA + PQ.
Phase 2: Gradual retirement of ECDSA
Over time, outputs move to pure PQ-only schemes.
Old outputs are swept into new formats under time pressure (“move your coins or they’re vulnerable”).
Performance in Phase 1:
Signature size: possibly 12–50x ECDSA overall for some scripts combining old+new.
Verification cost: significantly higher.
And because people are slow / unable / don’t want to migrate:
The hybrid era can drag on for years.
Meaning:
Bloated transactions,
Heavier chain growth per economic unit,
More bandwidth/CPU stress,
But no immediate benefit to everyday users (“it still works the same”).
This is ripe for:
“Quantum safety” as PR cover,
Real effect: raise technical barriers for sovereign users and small nodes.
9.6) Impact on Lightning and L2 / custodial
If L1 becomes:
Slower (effective TPS down),
Heavier (fee per “normal” payment goes up),
More resource-intensive (node floor increases),
Then:
Lightning Network:
Opening/closing channels becomes more expensive in bytes and fees.
LN topology may re-centralize around a few big hubs (they can afford the heavy L1 operations).
Small users:
Either trust hubs more,
Or get pushed to custodial LN (wallet-as-a-service).
Custodial & stablecoins:
If self-custody L1 + LN is technically and legally heavier, while:
Stablecoin/custodial offerings provide instant UX and regulatory blessing,
Then:
The path of least resistance is:
Custodial BTC (on exchanges, in ETFs),
Or just stablecoins / future CBDCs.
PQ upgrade, if done clumsily, becomes part of a “soft squeeze”:
self-custody becomes the hardest path (cost, legal risk, infra),
state-aligned rails become easiest (accounts, wallets, embedded stablecoins).
9.7) The incentives of the Controllers in this shift
Keep rails inspectable:
They prefer a world where:
Most BTC flows are on KYC exchanges, wrapped in ETFs, or on regulated L2s.
Nodes are concentrated enough to pressure infra (cloud providers, ISPs, data centers) if needed.
A badly designed quantum upgrade:
“Accidentally” pushes BTC further in that direction because:
Higher resource floor excludes small participants.
Bigger on-chain overhead makes retail L1 usage rare.
People default even more to custodial wrappers.
The story is “security” but the revealed outcome is:
more control over the surviving infra,
and more reliance on institutions.
9.8) So what does it concretely do to performance?
If we compress all of this into concrete performance changes for a serious PQ upgrade:
On-chain throughput (TPS):
Base case: effective TPS drops, unless:
Block size/weight is increased (centralization pressure),
Or usage migrates heavily to off-chain/custodial (more control).
Fee dynamics:
Larger tx size → higher minimum fee to get confirmed.
Everyday users get priced out of on-chain use faster in congestion.
Node performance & decentralization:
Higher disk, bandwidth, and CPU requirements.
Fewer truly independent home nodes.
More reliance on:
Pruned/light clients,
Commercial infra,
Big players running full nodes.
Lightning & L2:
Opening/closing channels becomes more expensive.
L2 becomes more important but more centralized/pseudo-custodial.
Everyday “BTC payments” are done on systems that look more like banks / fintech (and later CBDCs / walled gardens).
Operational complexity:
Migration logic, wallet UX, key management for PQ schemes.
More ways for users to shoot themselves in the foot (keys, scripts, addresses).
More engineering surface for bugs and exploits.
9.9) TL;DR on performance
A quantum-resistance upgrade is:
Security justification on the surface,
A performance + complexity trade-off underneath,
With built-in centralization risk if not aggressively minimized.
Most realistic outcomes:
L1 becomes more scarce, heavy, and “institutional”.
Sovereign usage persists, but:
It’s more expensive.
It requires more competence.
It’s easier to paint as “risky” or “suspicious”.
Custodial/ETF/stablecoin rails keep gaining share because they can abstract away the complexity and cost.
Pure performance verdict:
Transaction speed: block interval likely unchanged (10 minutes), but effective throughput per block down unless blocksize is expanded.
Storage: chain growth and UTXO size likely up significantly, especially in the mixed/hybrid period.
Bandwidth: block + tx relay heavier → higher entry cost for full nodes.
CPU: signature verification cost up, but less of a bottleneck than bandwidth/storage if engineered decently.
Any “quantum safety” deployed in a hasty / maximalist way risks doubling as a decentralization tax on the parts of Bitcoin the system least likes: cheap, sovereign, low-barrier self-custody.
The physics of post-quantum cryptography makes things heavier. What matters is who pays that cost, and who gets to stay on the default rails when the upgrade happens.
10) On freezing coins for “safety reasons”
Some people in the Bitcoin community have raised the question of freezing coins if others refuse to/are unable to/are slow to migrate to PQ addresses.
Just seriously entertaining “freezing non-migrated coins for their own safety” is already a massive Overton-window shift that undermines Bitcoin’s core social contract.
In my opinion:
a hard consensus-level freeze is low probability but not zero;
soft, de-facto freezes (via regulation, policy, and infrastructure) are much more likely.
If an actual freeze ever happens, Bitcoin as an uncompromisable, credibly neutral settlement layer is finished in principle, even if the ticker survives and appreciates in fiat terms.
10.1) What “freezing coins” actually means in practice
You have to separate three layers:
1) Hard consensus freeze
New rules that say: “Any UTXO that hasn’t moved to a PQC script type by block X is provably unspendable forever”.
That’s equivalent to a protocol-level confiscation, even if dressed up as “safety”.
2) Soft social/infra freeze
Miners, pools, or relay nodes treat spends from non-migrated outputs as non-standard or high-risk and deprioritize or reject them.
Exchanges refuse deposits from “legacy” ECDSA outputs after some date.
Custodians/ETFs refuse to accept “unsafe” UTXOs, effectively making them illiquid.
3) Regulatory/economic freeze
Laws and guidance label non-migrated coins as negligent or even illicit exposure.
Banks and brokers cannot touch them; insurers won’t cover them.
Tax or reporting penalties make moving them extremely painful.
From a holder’s perspective, (2) and (3) can feel almost the same as (1): you technically “own” the coins, but no one will accept them, and you’re legally exposed if you try to use them.
10.2) Implications of even raising the question of freezing coins
Just talking seriously about freezing non-migrated coins has big consequences:
1) It punctures the “your keys, your coins, forever” myth
The implicit social promise has always been:
If you control the private key, nobody can change the rules to take your coins.
Once the community starts saying:
“Well, maybe we should freeze some people’s coins for safety…”
you’ve admitted that social choice can override property rights.
2) It legitimizes the idea that devs/miners are stewards, not janitors
The strongest cypherpunk version: devs maintain code; miners order transactions; nobody decides who is “worthy” of coins.
Freezing for “safety” implicitly says:
“There exist legitimate reasons for protocol/social actors to judge some owners incompetent and override them.”
That’s exactly the logic regulators love: “incompetent public → guardians needed”.
3) It gives regulators rhetorical ammunition
Once the community admits “some coins should be immobilized to protect their owners”, it’s trivial for a regulator to extend that logic:
“If we can freeze for quantum safety, we can also freeze for AML, sanctions, child protection, terrorist risk, etc. It’s the same principle: we’re just protecting the system.”
That doesn’t mean Bitcoin instantly becomes a CBDC, but it softens resistance.
4) It splits the social layer along a very clear line
Hardcore sovereigns:
“Any freeze is theft. Period.”
Safety-pilled “pragmatists”:
“We have to protect normies from quantum theft; better we freeze than some hacker.”
This split is exactly the kind of wedge that can be exploited by states and large custodians: they align with the safety camp and paint the other side as extremist.
5) It damages the “credibly neutral” narrative in the eyes of serious outsiders
High-IQ allocators already see governance risk; this just confirms it:
“If enough social pressure builds, they will change the money rules, even if it’s dressed as security.”
That pushes BTC one notch further toward “governance-risk-laden speculative asset”, away from “hard, rule-bound collateral”.
Even if no freeze ever happens, the mere fact that this is on the table raises the perceived tail risk and should command a higher required risk premium for sovereign, long-horizon allocators.
10.3) How likely is an actual freeze?
We need to separate:
Hard consensus freeze probability
Soft/regulatory freeze probability
The Controllers likely want to contain-not-kill:
1) Hard consensus freeze (unspendable UTXOs after a deadline)
Very controversial for core culture.
Would invite chain splits and reputational carnage.
My rough, long-horizon (10–20y) guess: 5–10%.
It would likely only be seriously attempted in a “this or mass theft” framing (visible quantum break + stolen coins headlines).
2) Soft/infra/regulatory freeze (practically illiquid without using KYC intermediaries)
Much, much more likely.
Because it fits:
Incentives of regulators (“we want safe, trackable coins”).
Incentives of custodians (“we want AUM and fee streams”).
Incentives of big holders (“we want political cover if something breaks”).
This looks like:
“PQ-compliant coins” as a separate class with better banking rails.
Legacy coins technically spendable but heavily penalized or scary to move.
My guess: 30–50% probability over 10–20y of some form of de facto freeze/ostracization of legacy outputs, especially in the regulated West.
3) No freeze, but strong migration pressure
Also plausible: 40–60%.
Here you get:
Scary headlines about quantum.
Default wallet flows to PQ addresses.
Exchanges preferentially treat PQ outputs.
But no explicit freeze. Still centralization tilt, less explicit betrayal.
So formal “Great Taking” via hard freeze is a tail; soft capture through PQ migration pipelines is base-case-ish.
10.4) How this interacts with Bitcoin’s legitimacy
If you define Bitcoin’s core as:
Immutable rules,
No one can forcibly change spendability conditions of your coins without your consent,
“Your keys, your coins” as an absolute —
Then: any freeze crosses that line.
The Controllers’ perspective would be different:
“We didn’t seize anything.
We protected unsophisticated users from quantum theft.
We offered them free migration tools.
The community agreed to upgrade the rules democratically”.
But from the meta-layer:
That move proves that governance > immutability in practice.
Once the social layer has accepted one legitimate exception, you’ve normalized the logic:
“Some risks justify overriding property rights by social consensus.”
After that, the fight is not about whether coins are ever frozen again, but which justification is deemed sufficient:
Quantum risk today.
Sanctions risk tomorrow.
“Systemic stability” the day after.
Freezing coins invalidates the original idea, even if it doesn’t kill the asset.
10.5) How does this fit with the broader lens?
1) Incentives
The Controllers want:
Fewer truly sovereign, anonymous coins.
More identity-bound, custodian-held coins.
Narrative cover (“we’re protecting your savings from quantum hackers”).
Custodians/exchanges want:
Flow and AUM through their migration tools.
Safety-pilled devs want:
Not to be blamed for grandma’s lost coins if a quantum break hits.
2) Control
A PQ migration is the perfect choke point to:
Re-write the ownership graph.
Map balances to identities.
Establish new norms about whose coins are “up to code”.
3) Stability
Freezing some coins for “safety” can be sold as reinforcing stability (“we avoided mass theft”).
4) Truth
The actual quantum timeline can lag far behind the rhetoric and still be used to justify early migration campaigns.
5) Revealed preference
If you see serious actors pushing any flavor of freeze or de facto ostracization:
They are telling you they prefer a curated, governable ledger over a fully sovereign one.
Bitcoin’s role is being steered toward managed, surveilled, SoV-corridor asset.
10.6) So what does this mean in practice?
The mere existence of “freeze for safety” as a serious discourse:
Lowers the ceiling on Bitcoin’s claim to unimpeachable immutability.
Raises the probability that future “emergency fixes” will also be floated and, over time, normalized.
The most likely path is not:
“One day all legacy UTXOs are hard-frozen at block X, everything explodes.”
The more realistic path is:
Quantum threat used as narrative vector to:
Funnel people into compliant PQ custody.
Grow the paper layer (ETFs, custodians) relative to sovereign UTXOs.
Increase governance risk slowly while fiat price may still rise.
From the Core v30 fiasco, to more paperization, regulation, centralizationl, the Coordination tax is likely to strike again with Quantum FUD.
If you don’t design with the Coordination tax in mind, over time freedom goes down, even if number goes up.

Incredibly thorough breakdown of the coordination nightmare. The point about signature bloat essentially pricing out sovreign users while institutions absorb the cost hits hard. I've been watching how similar infrastructure upgrades in other protocols always seem to advantage the players with the deepest pockets, and this feels like another example where "safety" becomes a trojan horse for consolidation.